Question:
Windows seems to take forever to start up on both my computers, and some programs try to run everytime I start Windows (even though I didn’t ask them to). I’m running Windows Vista Home on a fairly new laptop with 512 mb of RAM, and Windows XP on an older desktop with 1GB of RAM. What can I do to speed things up?
Answer: Those extra programs take away time and precious memory, which makes Windows take longer to start up and also makes it run slower once Windows has started.
There are a couple of things you can do right away that will speed up Windows startup and stop those unwanted programs from running.
Clean out your Startup folder
Some programs will install themselves in your Windows Startup folder, which makes them run each time your system boots up. All you have to do is delete the menu shortcut, and they’ll stop loading when Windows starts up. The programs will still remain installed on your system – they just won’t run until you run them (which is what you want).
1. Right-click on the Start button in your task bar (lower left corner of your screen).
2. Select Explore from the shortcut menu.
3. You’ll see a folder called Startup, and you can delete all of the programs listed in this folder. You’ll only be deleting the menu shortcuts, not the programs themselves.
This is a good first step that’ll speed up Windows startup and free up memory on your system, but there are still a couple other things to check.
Defragment your hard drive
Over time your hard drive can become defragmented, which means that files get saved in different places on your hard drive. Windows can’t just look in the same general area each time it tries to find files, which slows things down noticeably, and can directly increase startup time.
 Windows comes with its own disk defragmentation tool, but it doesn’t work very well and you can’t schedule it to automatically defrag your hard drive on an ongoing basis.
Windows comes with its own disk defragmentation tool, but it doesn’t work very well and you can’t schedule it to automatically defrag your hard drive on an ongoing basis.
I use Diskeeper for that, which rearranges files stored on your disk to occupy contiguous storage locations. This speeds up access time because it can look in the same general area for files each time it needs them.
You can set Diskeeper to run automatically in the background so that you basically never have to worry about your hard drive slowing down due to defragmentation.
Turn off unnecessary services
Some programs create Windows services that run behind the scenes to check for updates online, or watch for system events like inserting a music CD in your CD drive. iTunes is one such program, and there are even spyware programs that can load at startup by installing themselves as a Windows service.
These services take up valuable memory, and considerably slow down Windows startup. For example, a program called Vongo was installed with my new laptop, and it tries to check for updated downloads every few minutes. This eats up processing time, takes up extra memory on my system, and poses a potential security risk to my system.
If you’re fairly technically inclined, you can view the services that are installed on your system and disable unwanted programs from loading at startup. All of the Windows services that are running on your system can be viewed by opening your Control Panel and selecting “Administrative Tools” and then “Services”.
But be careful, because if you turn off the wrong service you could end up rendering your system unusable.
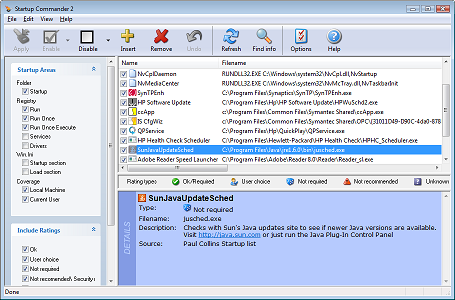
A safer way to control the services that run at startup is to use a program like SystemSuite 8 Professional . It will show you a list of all the services that are running on your system, and will identify the ones that are safe to turn off.
. It will show you a list of all the services that are running on your system, and will identify the ones that are safe to turn off.
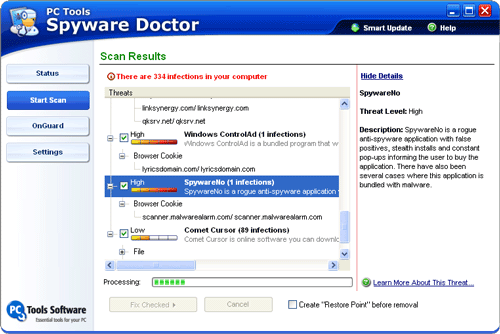
SystemSuite will also show you if there are any spyware or malware programs lurking on your system, and will let you protect your system by blocking them from loading when Windows starts up.
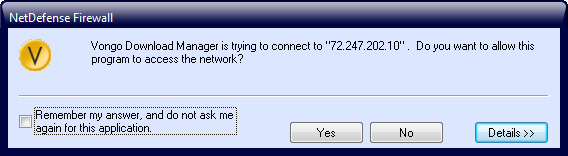
For example, SystemSuite’s built-in NetDefense Firewall recognized the Vongo program I mentioned earlier and asked me if I wanted to block it from connecting to the Internet in the future. I happily said yes to block it, and now I don’t have to worry about it connecting to the Internet in the future.
I’ve noticed a big improvement in startup time using these approaches, and especially with System Suite. It’s received some excellent reviews like this one from Laptop Magazine:
“Consistently better than any all-in-one-system-maintenance suite, Avanquest’s excellent collection has all the core strengths and exciting extras.” – Laptop Magazine July 2007
Let me know how it works for you.
Enter Coupon Code AFFSS8 during checkout to save 25% on SystemSuite 8.